Terraform (IaC) Automation-End-to-End Project
AWS EC2 Auto Scale -VPC-LB-SNS-CloudWatch
Terraform ❓
Terraform is an IAC tool that helps DevOps teams automate various infrastructure tasks. One of Terraforms primary use cases is provisioning cloud resources. HashiCorp developed a cloud-agnostic, open-source provisioning tool written in the Go language.
Why Terraform❓
Terraform Cloud offers remote state management, which securely saves and controls the state of your infrastructure, facilitating cooperation and preventing disputes. Terraform state files are encrypted at rest, and you can let specific teams and individuals to see these state files.
Project Overview 📰
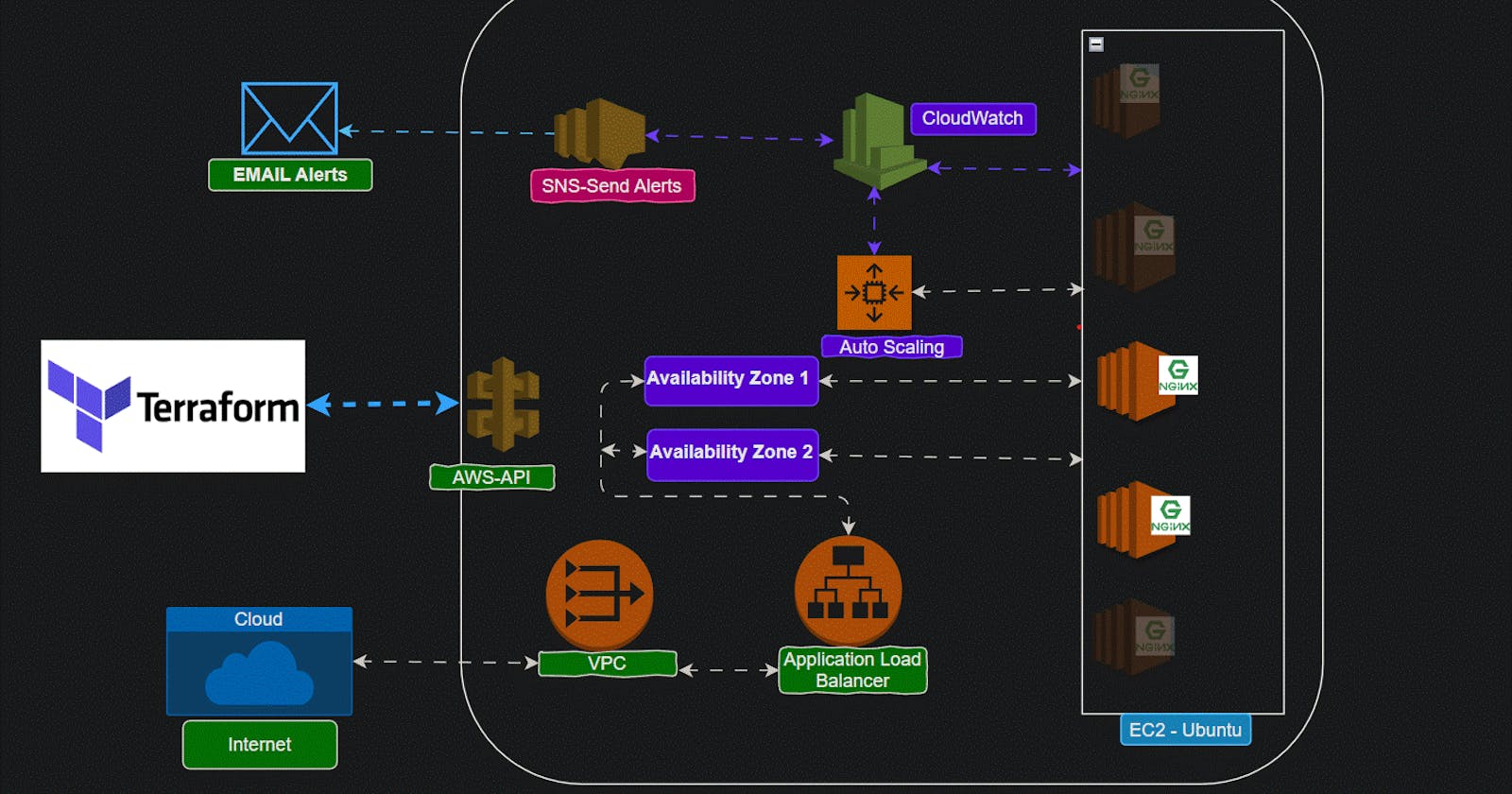
Using Terraform we are going to create AWS resources and we are monitoring the instances by cloud watch.
If EC2 instances CPU reaches 75% load , Cloud watch will trigger the Auto scale.
Once Auto scale triggered it will add one new instance in EC2.
If 5 mins avg load CPU reduced to 50%, Auto scale delete the one instance.
Auto scale Min instances = 2, Max=5, Desired=2
And SNS will notify the Auto scale activity via Email.
At Specific time in a day Auto Scale refresh the instance
Load balancer will added for all instances while create
load balancer connected two availability zone for High availability.
Project Link- GitHub: https://github.com/karthick-dkk/Terraform
Requirements: 📦
AWS-CLI
Configure AWS Access Key and Secret key
Terraform
AWS-CLI 💻
⬇️Download the AWS-CLI
curl "https://awscli.amazonaws.com/awscli-exe-linux-x86_64.zip" -o "awscliv2.zip"
Install aws-cli
unzip awscliv2.zip # unzip the files
sudo ./aws/install --bin-dir /usr/local/bin --install-dir /usr/local/aws-cli --update
Verify the installation
unzip awscliv2.zip && sudo ./aws/install
Configure AWS-CLI
Get you AWS access keys from AWS, by navigate to IAM-->user-->security credentials -->Add new keys.
Note: user need below permissions for perform this tasks
AWS EC2 full access
AWS VPC full access
AWS SNS full access
[root@centos7 test-5]: aws configure
AWS Access Key ID [****************CCCD]: <your Access key>
AWS Secret Access Key [****************02V1]: <your Secret Key>
Default region name [ap-south-1]: <region>
Default output format [jq]:
Install Terraform
Follow the below instructions for terraform installation
For Debian distributions
configure hashiCorp gpg key
sudo apt-get update && sudo apt-get install -y gnupg software-properties-common
wget -O- https://apt.releases.hashicorp.com/gpg | \
gpg --dearmor | \
sudo tee /usr/share/keyrings/hashicorp-archive-keyring.gpg
gpg --no-default-keyring \
--keyring /usr/share/keyrings/hashicorp-archive-keyring.gpg \
--fingerprint
Install terraform package
echo "deb [signed-by=/usr/share/keyrings/hashicorp-archive-keyring.gpg] \
https://apt.releases.hashicorp.com $(lsb_release -cs) main" | \
sudo tee /etc/apt/sources.list.d/hashicorp.list
sudo apt update
sudo apt-get install terraform
check the terraform --version for verify.
Download the Project files from GitHub
git clone https://github.com/karthick-dkk/Terraform
cd Terraform/aws/projects/ec2
Files Overview: 📜
app_tfvars - store the variables values.
variables - Assign the variable , type, default value
main.tf - Executable code file, modules
main.tf --> variabels.tf --> app_tfvars --> AWS API
You can modify the configurations as per your requirements.
Run Terraform 🗃️
Initialize the terraform for download the required plugins
terraform init
Test the config 🧪
terraform plan -var-file=app.tfvars
Apply the config ⛈️
terraform apply -var-file=app.tfvars
Note:
Do not remove terraform.tfstate files.
Terraform will save the current state, previous state , desired state on local file.
do not change the configurations from AWS console, once apply terraform , it will conflict .
Delete the terraform config 🗑️
terraform destroy -var-file=app.tfvars
Follow for more: ✌️
LinkedIn: https://www.linkedin.com/in/karthick-dkk/
Medium: https://karthidkk123.medium.com/
Github: https://github.com/karthick-dkk/
Hashnode: https://karthick-dk.hashnode.dev/
